#20250106
프로젝트 012
IDS(우분투 22.04)에 snort 설치
sudo apt update
sudo apt -y install snort
snort --version
--
cd /etc/snort/rules
sz *.rules
---
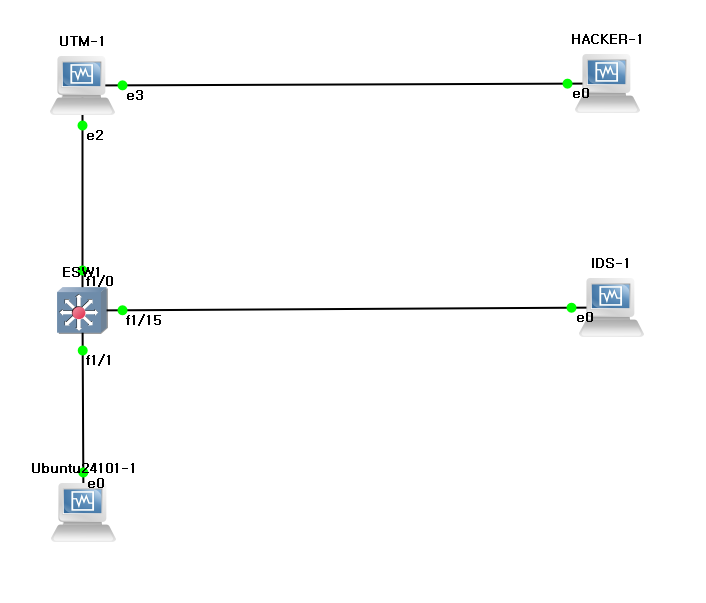
탐지 시스템
스위치에 포트미러링 설정
config t
monitor session 1 source interface fastethernet 1/0 - 14
monitor session 1 destination interface fastethernet 1/15
end
IDS에서 tcpdump 실행
tcpdump -i enp0s3
IDS
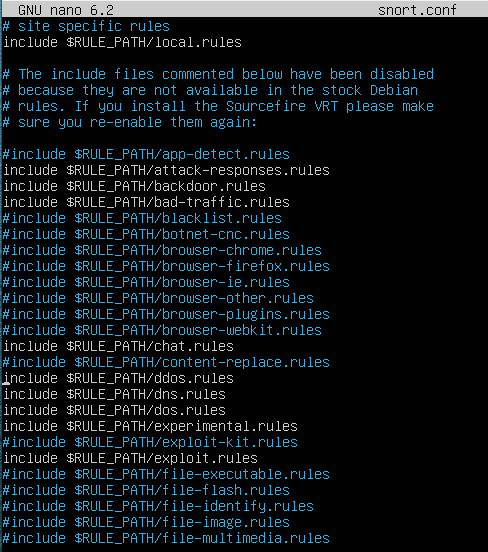
> nano /etc/snort/snort.conf
#Step 7
include $RULE_PATH/local.rules 제외 모든 .rule 주석처리 (Step 8 전까지)

> nano /etc/snort/rules/local.rules
alert icmp any any -> any any (msg:"DetectToIcmp"; sid:1000001
탐지 실행. (칼리에서 10.0.2.15에 ping 보내기)
 kali > ping 10.0.2.15
kali > ping 10.0.2.15
IDS > snort -A console -q -u snort -g snort -c /etc/snort/snort.conf
ICMP 플러딩 공격
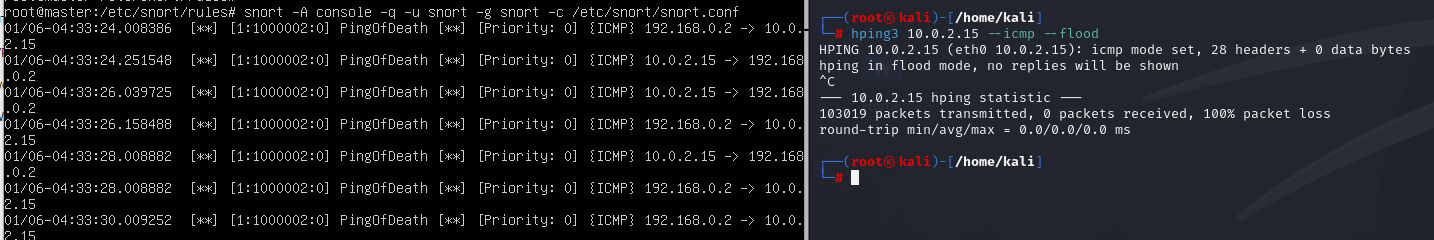 kali > hping3 10.0.2.15 --icmp --flood
kali > hping3 10.0.2.15 --icmp --flood
IDS local.rule > alert icmp any any -> any any (msg:"PingOfDeath";threshold:type both,track by_src,count 10,seconds 2;sid:1000002;)
nmap 공격
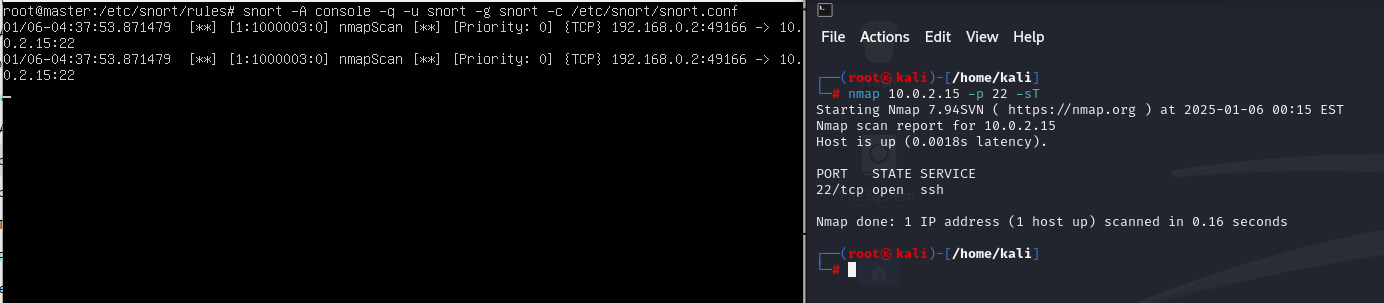 kali > nmap 10.0.2.15 -p 22 -sT
kali > nmap 10.0.2.15 -p 22 -sT
IDS local.rule > alert tcp any any -> 10.0.2.15 22 (msg:"nmapScan"; flags:S; sid:1000003;)
ssh 공격
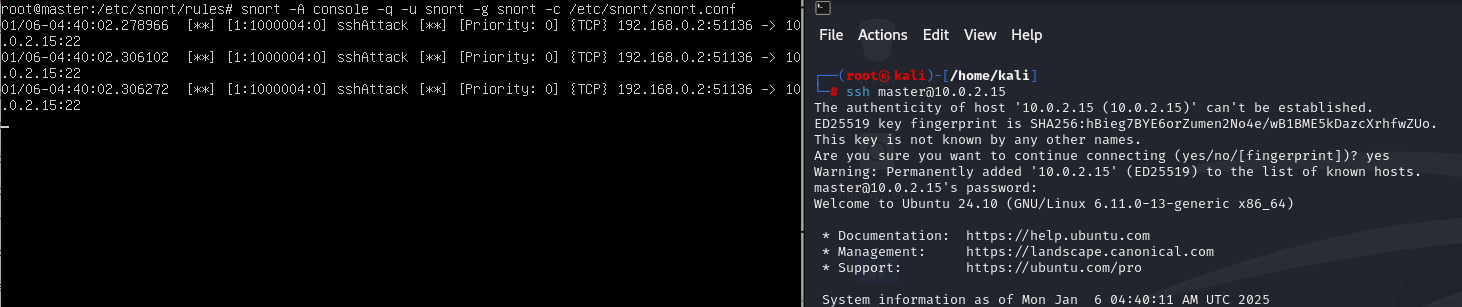 kali > ssh master@10.0.2.15
kali > ssh master@10.0.2.15
IDS local.rule > alert tcp any any -> 10.0.2.15 22 (msg:"sshAttack";content:"SSH";nocase;sid:1000004;)
hydra 공격
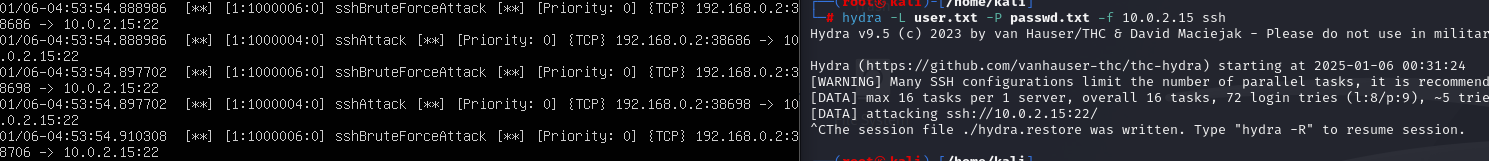 hydra -L user.txt -P pass.txt -f 10.0.2.15 ssh
hydra -L user.txt -P pass.txt -f 10.0.2.15 ssh
alert tcp any any -> 10.0.2.15 22 (msg:"sshBruteForceAttack";content:"SSH";nocase;offset:0;depth:4;sid:1000006;)
IDS 반야드(barnyard) 2 설치
IDS(우분투 22.04)에 snort 설치
sudo apt update
sudo apt -y install snort
snort --version
--
cd /etc/snort/rules
sz *.rules
---
탐지 시스템
스위치에 포트미러링 설정
config t
monitor session 1 source interface fastethernet 1/0 - 14
monitor session 1 destination interface fastethernet 1/15
end
IDS에서 tcpdump 실행
tcpdump -i enp0s3
IDS
> nano /etc/snort/snort.conf
#Step 7
include $RULE_PATH/local.rules 제외 모든 .rule 주석처리 (Step 8 전까지)
> nano /etc/snort/rules/local.rules
alert icmp any any -> any any (msg:"DetectToIcmp"; sid:1000001
탐지 실행. (칼리에서 10.0.2.15에 ping 보내기)
IDS > snort -A console -q -u snort -g snort -c /etc/snort/snort.conf
ICMP 플러딩 공격
IDS local.rule > alert icmp any any -> any any (msg:"PingOfDeath";threshold:type both,track by_src,count 10,seconds 2;sid:1000002;)
nmap 공격
IDS local.rule > alert tcp any any -> 10.0.2.15 22 (msg:"nmapScan"; flags:S; sid:1000003;)
ssh 공격
IDS local.rule > alert tcp any any -> 10.0.2.15 22 (msg:"sshAttack";content:"SSH";nocase;sid:1000004;)
hydra 공격
alert tcp any any -> 10.0.2.15 22 (msg:"sshBruteForceAttack";content:"SSH";nocase;offset:0;depth:4;sid:1000006;)
IDS 반야드(barnyard) 2 설치